services
We offer comprehensive services to secure and optimize your IT infrastructure. Our Cybersecurity solutions include network and endpoint security, threat intelligence, and incident response. Systems Engineering (SE) ensures efficient system design and performance optimization. Vulnerability Management (VM) involves assessments, patch management, and penetration testing to reduce risks. We also provide Cloud Security, Managed IT Solutions, and Enterprise Innovation services to drive digital transformation and enhance IT operations.
Protect
Your Business
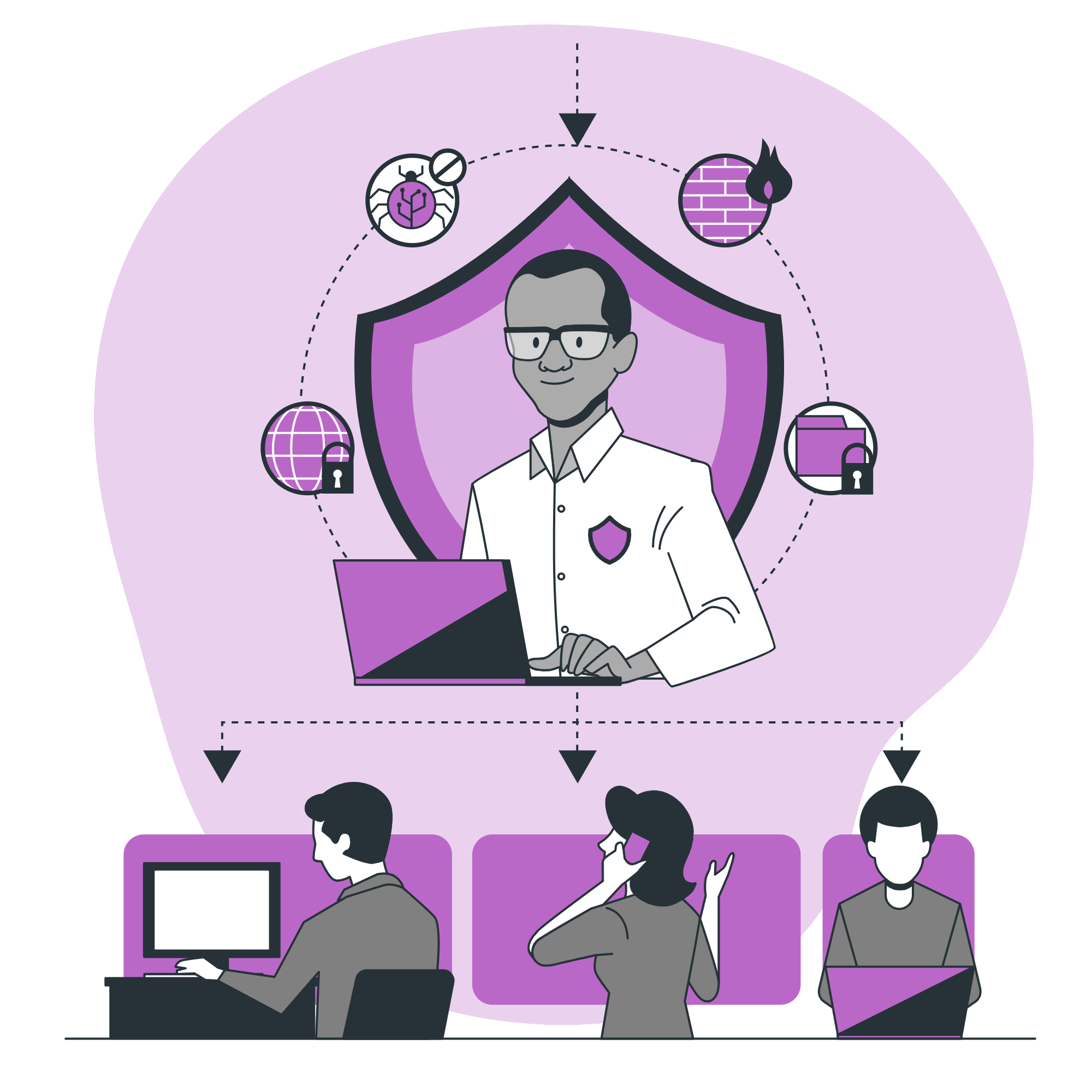
In today’s digital era, the safety of your business hinges not just on physical security but on robust cybersecurity measures. As cyber threats evolve and multiply, ensuring the integrity and confidentiality of your business data becomes paramount. Investing in cutting-edge cybersecurity solutions is no longer optional—it’s a necessity to thrive and instill trust in your clients and stakeholders. Protect your assets, reputation, and future with proactive cybersecurity measures.


Seamlessly integrating advanced threat detection

We offer top-notch defence against the most sophisticated cyber threats

Ensuring prompt responses to cybersecurity incidents
Our services encompass thorough assessment and robust protection to safeguard your digital assets against potential threats.
We specialize in timely detection of threats and provide swift response measures to ensure your system’s integrity and safety.

We facilitate sound governance strategies and ensure compliance with the latest industry standards and regulations
Protecting Your Digital World

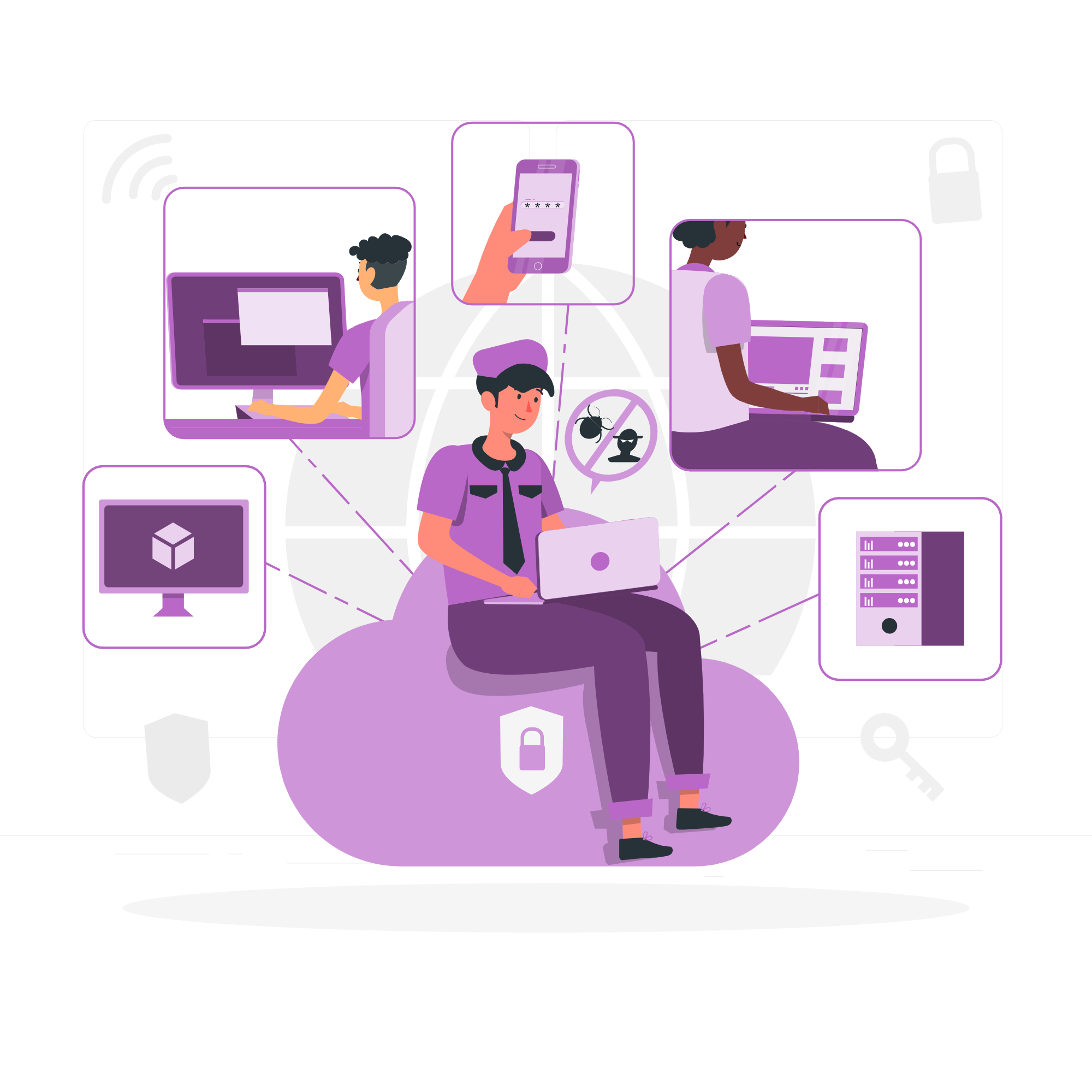
Managed IT Solutions involve entrusting the management and operation of an organization’s IT infrastructure to an external service provider. This typically includes a comprehensive suite of services such as network management, data backup and recovery, cybersecurity, and IT support. By partnering with a managed IT provider, businesses can focus on their core operations while leveraging the expertise of IT professionals who ensure that their systems are up-to-date, secure, and running efficiently. Managed IT Solutions often include proactive monitoring and maintenance, which helps in preventing issues before they arise. This approach can lead to significant cost savings, improved system performance, and enhanced security, as the provider brings specialized knowledge and resources that may be beyond the reach of an internal IT department.

Systems Engineering is a holistic approach to designing and managing complex systems throughout their life cycle. It involves integrating various components and subsystems to work together effectively to achieve specific objectives. Systems Engineers focus on defining requirements, analyzing system performance, and managing the entire system development process. This includes ensuring that hardware, software, processes, and people are all aligned and functioning seamlessly. Systems Engineering is critical in fields such as aerospace, defense, and large-scale IT projects, where the complexity of systems demands rigorous planning and coordination. By applying Systems Engineering principles, organizations can reduce risks, improve system reliability, and ensure that the end product meets both user needs and regulatory standards.

Vulnerability Management is a crucial aspect of cybersecurity that involves identifying, assessing, and addressing security weaknesses in an organization’s IT environment. The process begins with regular vulnerability scanning, which identifies potential security flaws in software, hardware, and network configurations. Once vulnerabilities are detected, they are prioritized based on their potential impact and exploitability. The next steps involve applying patches, reconfiguring systems, or implementing other remediation measures to address these weaknesses. Effective vulnerability management not only helps prevent cyber-attacks but also supports compliance with industry regulations and standards. By continuously monitoring and updating security measures, organizations can protect their assets from emerging threats and maintain a strong security posture.

Cybersecurity is a comprehensive field dedicated to protecting information technology systems, networks, and data from cyber threats. It involves implementing a wide array of protective measures, including firewalls, intrusion detection systems, and encryption technologies, to defend against attacks such as malware, ransomware, and phishing. Cybersecurity strategies focus on several key areas: prevention, to stop attacks before they occur; detection, to identify and respond to threats in real-time; and recovery, to restore systems and data after an incident. Effective cybersecurity requires continuous monitoring, regular updates, and employee training to recognize and respond to threats. It also involves developing and implementing incident response plans and disaster recovery strategies to minimize the impact of security breaches. In today’s digital landscape, where cyber threats are ever-evolving, a robust cybersecurity posture is essential for safeguarding sensitive information and maintaining trust with stakeholders.

Cloud Security encompasses a broad range of strategies and technologies designed to protect data, applications, and systems hosted in cloud environments. As organizations increasingly adopt cloud services, ensuring the security of these platforms becomes essential. Cloud Security practices include encryption of data both in transit and at rest, robust identity and access management to control user permissions, and regular security audits to identify potential vulnerabilities. Additionally, cloud security involves configuring cloud resources properly to prevent unauthorized access and using security tools to monitor for suspicious activities. Given the shared responsibility model in cloud computing, where both the cloud provider and the customer have roles in maintaining security, it is crucial for organizations to understand their security obligations and implement best practices to safeguard their cloud assets.

Have questions or need assistance?
Ready to take the next step in fortifying your cybersecurity posture? Contact us today to learn more about our services and how we can help you stay ahead of emerging threats in the ever-evolving cybersecurity landscape.
